Nick Savvides,
Security Advocate at Symantec Asia Pacific and Japan
Security Advocate at Symantec Asia Pacific and Japan
When
did WannaCry appear and how quickly did it spread?
did WannaCry appear and how quickly did it spread?
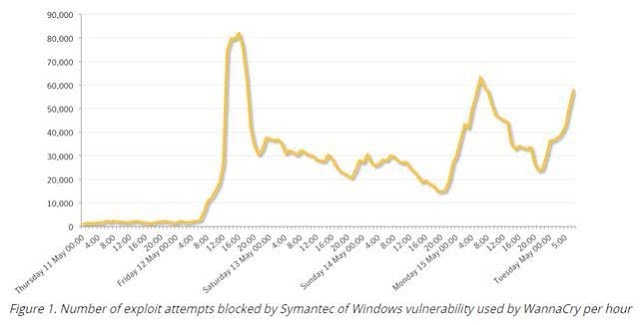
WannaCry first
appeared on Friday, May 12. Symantec saw a dramatic upsurge in the number of
attempts to exploit the Windows vulnerability used by WannaCry from
approximately 8:00 GMT onwards. The number of exploit attempts
blocked by Symantec dropped slightly on Saturday and Sunday but
remained quite high. Exploit numbers increased on Monday, presumably
as people returned to work after the weekend.
appeared on Friday, May 12. Symantec saw a dramatic upsurge in the number of
attempts to exploit the Windows vulnerability used by WannaCry from
approximately 8:00 GMT onwards. The number of exploit attempts
blocked by Symantec dropped slightly on Saturday and Sunday but
remained quite high. Exploit numbers increased on Monday, presumably
as people returned to work after the weekend.
Symantec blocks 22
million attempted WannaCry ransomware threats globally – full release here
million attempted WannaCry ransomware threats globally – full release here
- Symantec today reported it has blocked
nearly 22 million WannaCry infection attempts across 300,000
endpoints, providing full protection for Symantec customers through
its advanced exploit protection technology.
· Real-time
sharing of threat intelligence between endpoint and network systems – across
both Symantec Endpoint Protection and the Blue Coat ProxySG –
as well as machine learning technologies, helped ensure endpoint
customers were fully protected.
sharing of threat intelligence between endpoint and network systems – across
both Symantec Endpoint Protection and the Blue Coat ProxySG –
as well as machine learning technologies, helped ensure endpoint
customers were fully protected.
- Symantec Endpoint Protection and Norton
customers are fully protected from WannacCry by multiple layers of
advanced protection. This includes Symantec’s new advanced machine
learning, proactive network exploit protection, SONAR behavioral
protection, and the Intelligent Threat Cloud.
Do you see the situation escalating? If so what is the
best course of action from an overall corporate and country perspective in
order to mount a robust defence against these threats?
best course of action from an overall corporate and country perspective in
order to mount a robust defence against these threats?
This attack and variants
of it have the potential to escalate, as many organisations still haven’t
applied the patches to prevent the automatic spread. The best defense is to
ensure the operating systems and security software are up to date and
importantly educate users to exercise caution and understand the threats.
of it have the potential to escalate, as many organisations still haven’t
applied the patches to prevent the automatic spread. The best defense is to
ensure the operating systems and security software are up to date and
importantly educate users to exercise caution and understand the threats.
Best practices for
protecting against ransomware
protecting against ransomware
· Always keep your security software up to date to
protect yourself against them.
protect yourself against them.
· Keep your operating system and other software
updated. Software updates
will frequently include patches for newly discovered security vulnerabilities
that could be exploited by ransomware attackers.
updated. Software updates
will frequently include patches for newly discovered security vulnerabilities
that could be exploited by ransomware attackers.
· Email is one of the main infection
methods. Be wary of unexpected emails especially if they
contain links and/or attachments.
methods. Be wary of unexpected emails especially if they
contain links and/or attachments.
· Be extremely wary of any Microsoft Office email
attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a
genuine email from a trusted source, do not enable macros and instead
immediately delete the email.
attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a
genuine email from a trusted source, do not enable macros and instead
immediately delete the email.
· Backing up important data is the single most
effective way of combating ransomware infection. Attackers have leverage over their victims
by encrypting valuable files and leaving them inaccessible. If the victim has
backup copies, they can restore their files once the infection has been cleaned
up. However organizations should ensure that back-ups are appropriately
protected or stored off-line so that attackers can’t delete them.
effective way of combating ransomware infection. Attackers have leverage over their victims
by encrypting valuable files and leaving them inaccessible. If the victim has
backup copies, they can restore their files once the infection has been cleaned
up. However organizations should ensure that back-ups are appropriately
protected or stored off-line so that attackers can’t delete them.
· Using cloud services could help mitigate
ransomware infection, since many retain previous versions of files, allowing
you to “roll back” to the unencrypted form.
ransomware infection, since many retain previous versions of files, allowing
you to “roll back” to the unencrypted form.
Do you expect more such attacks to occur down the
road?
road?
Yes, ransomware is
extremely profitable for cyber-crimanls and we expect this to continue. The
profitability of ransomware has attracted new cyber-criminals to it, Symantec
research shows ransomware attacks grew to 463,841 in 2016, up
from 340,665 attacks in
2015 (36% increase) globally. The average ransom per victim grew
to $1,077 in 2016, up from $294 in 2015 (266% increase) globally.
extremely profitable for cyber-crimanls and we expect this to continue. The
profitability of ransomware has attracted new cyber-criminals to it, Symantec
research shows ransomware attacks grew to 463,841 in 2016, up
from 340,665 attacks in
2015 (36% increase) globally. The average ransom per victim grew
to $1,077 in 2016, up from $294 in 2015 (266% increase) globally.
Would you reckon that ransomware and APT attacks are
the most serious threats out there? Or do you see even more newer types of
cyber-attack tools be deployed?
the most serious threats out there? Or do you see even more newer types of
cyber-attack tools be deployed?
APTs and ransomware are
both very serious threats but operate at different ends of the cyber-crime
spectrum. Ransomware is generally indiscriminate with the idea to infect as
many people as possible to improve the chances of the ransom being paid as the motivation
is purely financial. APTs on the other hand are extremely targeted, they are
motivated by both money and politics. The cyber-criminals spend a lot of time
planning their APTs and use very sophisticated tools to achieve their goals.
Symantec expects both types of attacks to continue to evolve, to not just
improve their ability to compromise but also their ability to evade detection
both very serious threats but operate at different ends of the cyber-crime
spectrum. Ransomware is generally indiscriminate with the idea to infect as
many people as possible to improve the chances of the ransom being paid as the motivation
is purely financial. APTs on the other hand are extremely targeted, they are
motivated by both money and politics. The cyber-criminals spend a lot of time
planning their APTs and use very sophisticated tools to achieve their goals.
Symantec expects both types of attacks to continue to evolve, to not just
improve their ability to compromise but also their ability to evade detection
How many cases of
WannaCry has Symantec seen? How many clients has it helped currently? Did any
of them pay up?
WannaCry has Symantec seen? How many clients has it helped currently? Did any
of them pay up?
- Symantec does not actively
monitor the number of WannaCry cases. The speed at which this strain of
ransomware can infect users makes it extremely difficult to predict the
extent of this infection. - Symantec recommends affected
users not to pay the ransom. Paying
criminals is never recommended, as it feeds them and rewards them for
their crimes. There is also no guarantee that your files will be released
back to you.
We hear that WannaCry
is a hybrid of a worm and ransomware – how does it make the malware more
potent? What’s the worst case scenario this malware can have on society?
is a hybrid of a worm and ransomware – how does it make the malware more
potent? What’s the worst case scenario this malware can have on society?
WannaCry has the ability to spread itself
within corporate networks, without user interaction, by exploiting a known
vulnerability in Microsoft Windows.
within corporate networks, without user interaction, by exploiting a known
vulnerability in Microsoft Windows.
- Computers which do not have the
latest Windows security updates applied are at risk of infection.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!